-
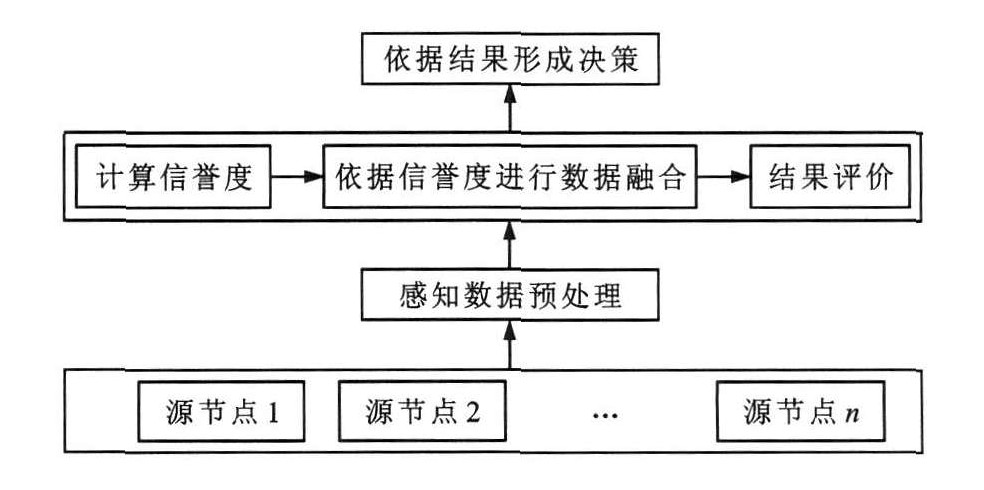
摘要: 引入了主观信任评价及其期望概率的概念, 通过统计方法评估船联网中各个节点的可信程度, 结合KL距离计算节点的信誉度, 从而建立了基于节点信誉度评价的数据融合信任模型。为避免影响融合的结果, 模型在数据融合过程中保留信誉度较好的节点, 摒弃低信誉的节点。模拟船联网网络结构进行仿真试验, 分别采用4种不同的攻击方法对网络中部分节点进行攻击, 试验分别按迭代100、200、300次进行。仿真结果表明: 传统方法的数据融合准确率为78%, 信任模型的数据融合准确率达到93%, 结果更逼近真实数据, 与传统方法相比有效提高了融合的准确性和可靠性。Abstract: The concepts of subjective trust elevation and its expected probability were introduced. The credibility value of every node in the internet of ships was evaluated by statistical method, and calculated by using KL divergence. A trust model of data fusion was proposed based on node credibility evaluation.The nodes with high credibilities were included in the model, however, the nodes with low credibilities were abandoned in order to avoid their effects in data fusion. The structure of internet of ships was simulated, four different kinds of attacks were adopted to attack some network nodes, and simulation experiments were done where the iteration numbers were 100, 200 and 300 respectively. Simulation result shows that data fusion accuracy is 78% by using traditional method, and fusion result by using trust model is nearer to true data with an accuracy of 93%. Compared with traditional method, the accuracy and security of data fusion are efficiently improved by trust model.
-
Key words:
- internet of things /
- internet of ships /
- data fusion /
- trust model /
- trust evaluation /
- KL divergence /
- credibility
-
表 1 攻击统计
Table 1. Attacking statistics
攻击类型 被捕获节点发送伪造数据比例/% 伪造数据情况 恶意行为类别 1 100 易察觉 直接恶意 2 100 不易察觉 掩饰恶意 3 65 易察觉 直接恶意 4 65 不易察觉 掩饰恶意 -
[1] ATZORI L, IERA A, MORABITO G. The internet ofthings: a survey[J]. Computer Networks, 2010(54): 2787-2805. [2] 胡向东. 物联网研究与发展综述[J]. 数字通信, 2010, 37(2): 17-21. doi: 10.3969/j.issn.1005-3824.2010.02.004HU Xiang-dong. Advance in research and development on the internet of things[J]. Digital Communication, 2010, 37(2): 17-21. (in Chinese). doi: 10.3969/j.issn.1005-3824.2010.02.004 [3] 宋亚辉, 李凤保, 李在铭. 无线传感器网络能效技术综述[J]. 仪器仪表学报, 2006, 27(6): 1665-1674. https://www.cnki.com.cn/Article/CJFDTOTAL-YQXB2006S2268.htmSONG Ya-hui, LI Feng-bao, LI Zai-ming. Survey on energy-efficiency technology for wireless sensor networks[J]. Chinese Journal of Scientific Instrument, 2006, 27(6): 1665-1674. (in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-YQXB2006S2268.htm [4] 唐慧, 胡向东. 无线传感器网络数据融合研究综述[J]. 信息安全与通信保密, 2007(7): 62-64, 68. doi: 10.3969/j.issn.1009-8054.2007.07.034TANG Hui, HU Xiang-dong. The research overview of data fusion in WSN[J]. Information Security and Communications Privacy, 2007(7): 62-64, 68. (in Chinese). doi: 10.3969/j.issn.1009-8054.2007.07.034 [5] KUMAR D, ASERI T C, PATEL R B. Energy efficient clustering and data aggregation protocol for heterogeneous wireless sensor networks[J]. International Journal of Computers, Communications and Control, 2011, 5(1): 113-124. [6] 周鸣争, 楚宁, 周涛, 等. 一种基于能量约束的传感器网络动态数据融合算法[J]. 仪器仪表学报, 2007, 28(1): 172-175. doi: 10.3321/j.issn:0254-3087.2007.01.035ZHOU Ming-zheng, CHU Ning, ZHOU Tao, et al. Dynamic data fusion algorithm based on energy restraining in sensor network[J]. Chinese Journal of Scientific Instrument, 2007, 28(1): 172-175. (in Chinese). doi: 10.3321/j.issn:0254-3087.2007.01.035 [7] GUO Jiang-hong, LUO Yu-dong. Probabilistic transmitting-based data aggregation scheme for wireless sensor networks[C]∥IEEE. Proceedings of the 2nd International Conference on Systems Engineering and Modeling. Paris: IEEE, 2013: 976-979. [8] MARAIYA K, KANT K, GUPTA N. Wireless sensor net-work: a review on data aggregation[J]. International Journal of Scientific and Engineering Research, 2011, 2(4): 1-6. [9] 赦文江, 武捷. 物联网技术安全问题探析[J]. 信息网络安全, 2010(1): 49-50. doi: 10.3969/j.issn.1671-1122.2010.01.013HAO Wen-jiang, WU Jie. Research on security of the internet ofthings[J]. Netinfo Security, 2010(1): 49-50. (in Chinese). doi: 10.3969/j.issn.1671-1122.2010.01.013 [10] 田俊峰, 鲁玉臻, 李宁. 基于推荐的信任链管理模型[J]. 通信学报, 2011, 32(10): 1-9. doi: 10.3969/j.issn.1000-436X.2011.10.001TIAN Jun-feng, LU Yu-zhen, LI Ning. Trust chain management model based on recommendation[J]. Journal on Communications, 2011, 32(10): 1-9. (in Chinese). doi: 10.3969/j.issn.1000-436X.2011.10.001 [11] 陈晶, 杜瑞颖, 王丽娜, 等. 网络环境下一种基于概率密度的信任博弈模型[J]. 电子学报, 2010, 38(2): 427-433. https://www.cnki.com.cn/Article/CJFDTOTAL-DZXU201002028.htmCHEN Jing, DU Rui-ying, WANG Li-na, et al. A trust game method basing on probability model in networks[J]. Acta Electronica Sinica, 2010, 38(2): 427-433. (in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-DZXU201002028.htm [12] CHEN Dong, CHANG Gui-ran, SUN Da-wei, et al. TRMloT: a trust management model based on fuzzy reputation for internet of things[J]. Computer Science and Information Systems, 2011, 8(4): 1207-1228. doi: 10.2298/CSIS110303056C [13] CEOLIN D, HAGE W R, FOKKINK W. A trust model to estimate the quality of annotations using the web[C]∥ACM. 2010 Web Science Conference. Raleigh: ACM, 2010: 1-8. [14] 刘文懋, 殷丽华, 方滨兴, 等. 物联网环境下的信任机制研究[J]. 计算机学报, 2012, 35(5): 847-855. https://www.cnki.com.cn/Article/CJFDTOTAL-JSJX201205002.htmLIU Wen-mao, YIN Li-hua, FANG Bin-xing, et al. A hierarchical trust model for the internet of things[J]. Chinese Journal of Computers, 2012, 35(5): 847-855. (in Chinese). https://www.cnki.com.cn/Article/CJFDTOTAL-JSJX201205002.htm [15] 袁禄来, 曾国荪, 姜黎立, 等. 网格环境下基于信任模型的动态级调度[J]. 计算机学报, 2006, 29(7): 1217-1224. doi: 10.3321/j.issn:0254-4164.2006.07.023YUAN Lu-lai, ZENG Guo-sun, JIANG Li-li, et al. Dynamic level scheduling based on trust model in grid computing[J]. Chinese Journal of Computers, 2006, 29(7): 1217-1224. (in Chinese). doi: 10.3321/j.issn:0254-4164.2006.07.023 [16] FANG Hui, ZHANG Jie, THALMANN N M. A trust model stemmed from the diffusion theory for opinion evaluation[C]∥IEEE. Proceedings of the 12th International Conference on Autonomous Agents and Multi-agent Systems. Saint Paul: IEEE, 2013: 1-8. [17] KIM H, LEE H, KIM W, et al. A trust evaluation model for QoS guarantee in cloud systems[J]. International Journal of Grid and Distributed Computing, 2010, 3(1): 1-9. -





 下载:
下载: